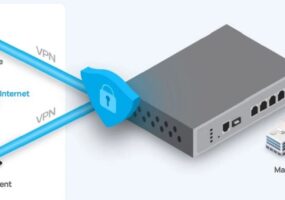
EnGenius Launches SD-WAN Gateway Series Products for Cloud-Based Networks
EnGenius, the Costa Mesa, Calif.-based networking and cloud solutions provider, recently launched its lineup of SD-WAN Gateway products, catering to the need for cloud-based services to prioritize security and efficiency for connecting any enterprise with its branch offices. The EnGenius SD-WAN series provides a secure and reliable solution, enabling seamless integration with EnGenius Cloud-managed Access […]











