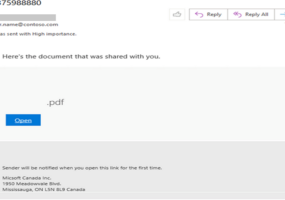
Microsoft Warns of Increasing Use of MFA Bypass Tools in Phishing Attacks
Microsoft is warning organizations of an uptick in Adversary-in-the-Middle (AiTM) phishing kits that are capable of bypassing multi-factor authentication (MFA) through reverse-proxy functionality, rendering the security tool that many organizations now deploy useless. In a new blog, the Microsoft Threat Intelligence Team dives into a threat actor it calls DEV-1101, a group that develops, supports […]











