Microsoft is hoping to address the security issue of emails sent to Exchange online from unsupported and unpatched Exchange Servers by enabling a transport-based enforcement system in Exchange Online that will throttle and then block emails from an unsupported server. The end goal is to encourage Microsoft customers to stop using persistently vulnerable versions of […]
Latest Content
Sony Electronics Launches 4K HDR Monitor BVM-HX3110
Sony's BVM-HX3110 monitor boasts new panel technology for improved brightness while maintaining pristine black reproduction.
Sony Electronics announced the launch of BVM-HX3110, a premium 30.5-inch, 4K HDR professional monitor for critical evaluation, color grading, live production and post-production. The monitor features a Sony-designed dual layer anti-reflection LCD panel with Sony proprietary signal processing. According to Sony, it thus supports a higher peak luminance of up to 4000cd/m² while maintaining no-compromise […]
The Alleged U.S. Military Document Leaker Worked in IT
The Air National Guardsman and IT worker arrested for leaking sensitive documents is a reminder to take insider risk seriously.
The FBI has arrested an alleged leaker of sensitive and highly classified U.S. military documents on the Ukraine-Russia conflict, arresting a 21-year-old Massachusetts Air National Guardsman and accusing him of posting the documents on a Discord server. That individual, Jack Teixeira, was an IT worker for the Air National Guard, working as a Cyber Defense […]
Audioconferencing Systems from Nureva Now Integrates with Extron
Nureva's HDL300 and Dual HDL300 audioconferencing systems now integrate with Extron's control and automation solutions to deliver camera-tracking features.
Nureva Inc., the Alberta, Canada-based innovator of IT-first audioconferencing solutions, announced that its HDL300 and Dual HDL300 audioconferencing systems now integrate with Extron control and automation solutions to deliver camera-tracking features that support hybrid working and learning. Extron used Nureva’s sound-location device API, available through Nureva Developer Toolkit, to update the Extron Control Systems Driver. . […]
Telelogos Approved as First Remote Solution for Philips Tableaux Displays
The latest collaboration between PPDS and Telelogos provides a content and device management solution for the new Philips Tableaux series.
PPDS, global provider of Philips professional displays, announced the approval of Telelogos software as the very first remote device-management solution for the new Philips Tableaux range of Advanced Colour ePaper displays. Per the company, the Philips Tableaux ePaper displays have opened up a new era of digital signage displays. Here, the innovative series has helped […]
Windows 11, New Features Coming to HoloLens 2
Microsoft is bringing Windows 11 to HoloLens 2, adding new security and collaboration features to the industrial mixed reality solution.
Microsoft is bringing Windows 11 to HoloLens 2, adding the security, collaboration and other features of the company’s newest operating system to its industrial metaverse and mixed reality solution. According to Microsoft, security was a major driver in bringing Windows 11 to HoloLens 2, helping users of the mixed reality solution feel confident when building […]
Honeywell Building Technologies Earns ISA/IEC Cybersecurity Certification
Honeywell Building Technologies (HBT) is now ISA/IEC 62443-4-1 Process Certified for its software development lifecycle.
Honeywell Building Technologies (HBT) has earned ISA/IEC 62443-4-1 Process Certification for its software development lifecycle. The ISA/IEC 62443-4-1 certification underscores HBT’s commitment to following best practices and standards in developing secure, cyber-resilient products, says the company. What are the ISA/IEC 62443 standards? The ISA/IEC 62443 standards define requirements and processes for implementing and maintaining electronically […]
Armorblox: BEC Attacks Increased by 72% YOY
BEC attacks surged 72% YoY with companies being targeted by language-based and socially engineered attacks across industries, finds Armorblox.
Threat researchers at email security firm Armorblox have found that business email compromise (BEC) attacks have increased dramatically by 72% year-over-year. In its second, annual 2023 Email Security Threat Report, the company says it continues to see high volumes of language-based and socially engineered attacks targeting organizations of all sizes and across industries. Vendor compromise […]
Software Manufacturers Urged to Think Security Before Features, Speed to Market
CISA and other cybersecurity agencies are urging tech companies to think more about security of their products.
The U.S. Cybersecurity and Infrastructure Security Agency along with its counterpart agencies from several different countries have published a new guide urging software manufacturers to take steps to ship products that are built with security from the ground up. The guidance, “Shifting the Balance of Cybersecurity Risk: Principles and Approaches for Security-by-Design and -Default, comes […]
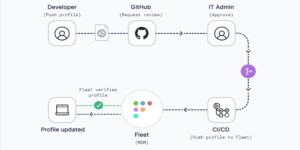
Fleet Launches Open-Source, Cross-Platform MDM Solution
The Fleet mobile device management solution has out-of-the-box support for macOS, Windows, Linux and ChromeOS.
FleetDM, a provider of open-source mobile device management solutions, is launching a new cross-platform programmable device management solution designed to give medium-to-large organizations control of remote workstation security with GitOps and workflow automation. The San Francisco-based company bills the mobile device management (MDM) solution as more accessible and cost-effective, but also scalable and customizable for […]