
Who Got Hacked This Week? June 24 Edition
What types of cyberattacks were carried out this week, June 24, 2019? Read on to find out about the latest cyberattacks and who got hacked this week.

June 24, 2019 Jonathan Blackwood Leave a Comment
What types of cyberattacks were carried out this week, June 24, 2019? Read on to find out about the latest cyberattacks and who got hacked this week.

June 20, 2019 Adam Forziati Leave a Comment
Over half of small businesses in the U.S. said they’ve experienced some kind of cyberattack within the past 12 months, says a Hiscox Cyber Readiness Report. Yet many lack a way to alert, diagnose, and solve these security concerns in a holistic way — and for a reasonable price. Recent funding gained by Defendify, a SaaS-delivered […]

June 20, 2019 Adam Forziati Leave a Comment
IBM says in a study that the cost of lost business after a breach for US organizations is $4.2 million. It is evident, then, that the organizations involved in the 5 biggest data breaches in 2019 thus far will likely suffer a considerable economic blow. But if you read this data breaches list thinking, “these are mega-companies; the risk of a data […]
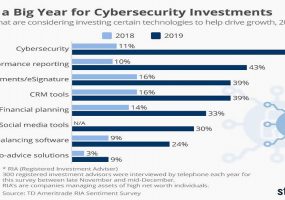
June 19, 2019 TechDecisions Staff Leave a Comment
Gone are the days of “Trust but Verify,” the framework made obsolete by an increasingly-malicious digital threatscape, says cloud columnist Louis Columbus in this Forbes article. Now, he says, it’s all about “Zero Trust Security,” something that emphasizes a “never trust, always verify, enforce least privilege” approach to cybersecurity. In his article, Columbus exemplifies ten cybersecurity […]

June 18, 2019 Sam Harton Leave a Comment
Despite the fact that scandals relating to cybersecurity and privacy policy riddled headlines following the presidential election, there has been little federal reform in those realms.

June 10, 2019 Lisa Montgomery Leave a Comment
A new concept implemented by Software Improvement Group aims to improve software security and health.

June 3, 2019 Jonathan Blackwood Leave a Comment
What types of cyberattacks were carried out this week, June 3, 2019? Read on to find out about the latest cyberattacks and who got hacked this week.

May 30, 2019 Lisa Montgomery Leave a Comment
Threat detection, investigation and incident response provide companies with greater detail about potential cybercrime.

May 23, 2019 Jonathan Blackwood Leave a Comment
What types of cyberattacks were carried out this week, May 23, 2019? Read on to find out about the latest cyberattacks and who got hacked this week.

May 23, 2019 Jessica Messier Leave a Comment
The university’s hacker-resistant development changes code and seals off network vulnerabilities faster than ever.

FREE Downloadable resources from TechDecisions provide timely insight into the issues that IT, A/V, and Security end-users, managers, and decision makers are facing in commercial, corporate, education, institutional, and other vertical markets
View all Guides
Get your latest project featured on TechDecisions Project of the Week. Submit your work once and it will be eligible for all upcoming weeks.
Enter Today!