Smart cities are quickly becoming a reality, with many cities around the globe introducing internet of things (IoT) devices into everyday operations in order to improve their communities. Check out some of the top smart cities in this infographic.
Latest Content
You Think You Have Cybersecurity Woes? So Does the Military
The military is working to keep its equipment and networks safe from hackers, including its F-35 aircraft.
The military is working to keep its equipment and networks safe from hackers, including its F-35 aircraft.
AWS Spot Instance and Cloud Security
All cloud providers have some type of a compute product offering which lets the user bid for the resource they need to complete or for more tasks. Amazon web services has led the way, offering a low cost EC2 usage option called Spot Instance. The model is unusual in the sense that tests the true limits of fault tolerance and unexpected interruptions in a software.
All cloud providers have some type of a compute product offering which lets the user bid for the resource they need to complete or for more tasks. Amazon web services has led the way, offering a low cost EC2 usage option called Spot Instance. The model is unusual in the sense that tests the true limits of fault tolerance and unexpected interruptions in a software.
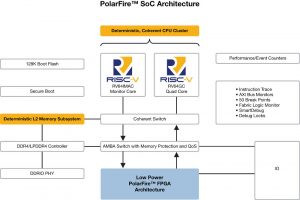
Linux Gets a Boost from First RISC-V SoC FPGA Architecture
Performance benefits from Linux operating systems provided by integration of PolarFire SoC’s hard CPU subsystem with programmable logic.
Performance benefits from Linux operating systems provided by integration of PolarFire SoC’s hard CPU subsystem with programmable logic.
Robot Floor Scrubbers to Join Walmart
Powered by BrainOS, robot floor scrubbers will be deployed to Walmart retail locations by early 2019.
Powered by BrainOS, robot floor scrubbers will be deployed to Walmart retail locations by early 2019.
Annual AWS re:Invent Event Utilizes CenturyLink for Cloud Connectivity
CenturyLink brings network and cloud connectivity to one of the world’s largest tech events.
CenturyLink brings network and cloud connectivity to one of the world’s largest tech events.
Fake Fingerprints Show Vulnerabilities in Security Measures
A group of researchers at NYU developed artificial fingerprints that were able to closely match real ones, demonstrating a possible weakness in fingerprint security methods.
A group of researchers at NYU developed artificial fingerprints that were able to closely match real ones, demonstrating a possible weakness in fingerprint security methods.
5 Key Tech Trends to Expect in 2019
Dimension Data recently released its Tech Trends 2019 report, and we spoke to the company to understand more about some key trends to expect in the new year.
Dimension Data recently released its Tech Trends 2019 report, and we spoke to the company to understand more about some key trends to expect in the new year.
Improve Customer Engagement with Password-Free Account Access
Averon MagicLogin eliminates the need for passwords and lengthy account setup to increase conversion rates and customer engagement.
Averon MagicLogin eliminates the need for passwords and lengthy account setup to increase conversion rates and customer engagement.
Overcome the Challenges of Deploying Artificial Intelligence
Peak offers a beta program to help organizations implement artificial intelligence successfully.
Peak offers a beta program to help organizations implement artificial intelligence successfully.