New Threat Intelligence Service from Barracuda
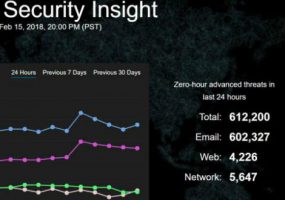
Barracuda Security Insight draws on data collected from Barracuda endpoints to provide real-time cybersecurity threat level measurements and more detailed information.
Barracuda Security Insight draws on data collected from Barracuda endpoints to provide real-time cybersecurity threat level measurements and more detailed information.










