With thousands of new software vulnerabilities to protect against each year, it is critical that organizations develop a robust vulnerability management program that can quickly identify and remediate vulnerabilities in IT environments.
Issues like Log4Shell, PrintNightmare, ProxyLogon and dozens of other critical vulnerabilities in widely used systems have kept IT departments up at night as they are on the frontlines against cybercriminals and nation-state hackers.
According to Max Pruger, general manager, compliance manager at Kaseya, there were an estimated 20,000 new vulnerabilities identified in 2021 alone, and that’s on top of the tens of thousands of older vulnerabilities that are still being used today.
The U.S. Cybersecurity and Infrastructure Security Agency since November 2021 has been keeping a list of vulnerabilities that are under active exploitation, many of which are more than a decade old. According to the database of 602 CVEs, 22 of actively exploited security bugs were first discovered in 2010 or earlier.
While zero day vulnerabilities can be difficult to manage given the urgency required to remediate bugs like Log4Shell, it’s those older vulnerabilities that should be neatly buttoned up and fixed before an enterprising criminal group scans for exploitable vulnerabilities.
“These are known vulnerabilities that are out there for several years that individuals just haven’t patched or haven’t addressed, mostly because they’re not doing proactive vulnerability scanning on their environment,” Pruger says.
Identify where the threats are coming from
When it comes to vulnerability management, organizations should first identify where the threats are coming from. According to Pruger, IT teams should prioritize external vulnerabilities, or software bugs that could allow an external attacker to gain access to your IT environment.
According to Pruger, this includes things like standard IP ports, external websites, authentication services and more.
“Anything that’s available to anybody externally,” Pruger says. “Those things are being hacked and attacked and scanned every second of every single day.”
While attacks originating from outside the network should take precedence, organizations should also be on the lookout for internal threats, such as a malicious application or Trojan downloaded to an end user’s device.
Which vulnerabilities to tackle first
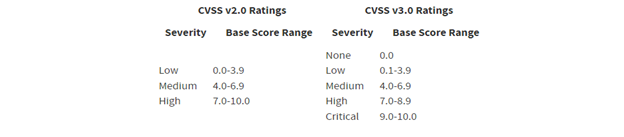
Generally, vulnerabilities with higher scores in the Common Vulnerability Scoring System (CVSS) should be remediated first. CVSS is an open standard widely adopted by the IT industry to assign levels of severity to vulnerabilities, with scores ranging from 0 to 10.
According to NIST, the National Vulnerability Database provides two versions of CVSS scores: V 2.0 and v3.x standards, including base scores that represent the innate characteristics of each vulnerability.
This table provides qualitative ratings of low, medium and high for both versions.
Many vulnerability scanners generate a lot of noise, which can make vulnerability management seem daunting at first, Pruger says.
“If you are scanning A range of IP on so you get a Class C, that’s 255 some odd IPs at 65,000 ports per IP,” Pruger says. “And depending on what field you’re using, you can have 65,000 potential vulnerabilities per port.”
With the sheer number of potential vulnerabilities in an IT environment, administrators should start with the more critical vulnerabilities. For example, Log4Shell – the critical vulnerability in the popular Java logger Logj — was assigned a CVSS of 10.
“It doesn’t get any higher than that,” Pruger says. “So, you want to try to address that one as quickly as possible.”
As a rule of thumb, any critical vulnerabilities should be prioritized as soon as IT admins are comfortable that the vendor’s patches work and won’t break anything in their environment.
Other less severe vulnerabilities (high or medium) should be treated just as importantly, but admins should take more time to test the patches in a staging environment that’s separated from the corporate network to ensure they won’t cause even more issues. Give the IT ecosystem a few weeks to roll out and test the patches, Pruger says.
For vulnerabilities with a CVSS of under 4.0, organizations can address those in a more staggered approach a handful of times per year, Pruger says.
Develop a standard scanning and patching schedule
Vulnerability management and scanning for security bugs in IT environments should be a regular practice of any IT team, but there are differing opinions on how frequently to conduct scans for vulnerabilities that could lead to compromise.
The general consensus among IT vendors and industry associations is that vulnerability scans should be conducted at least quarterly. However, Pruger says monthly scans are more effective at identifying vulnerabilities before they become issues.
However, IT professionals should also be paying attention to vendor updates, as they commonly fix critical vulnerabilities in widely used products. Scans should be run on an ad hoc basis to address zero days as soon as possible if the organization suspects that they are running impacted versions of the product.
“When the next Log4j 2.0 comes out, you’ve gotta go and run the scan across your entire environment,” Pruger says.
If you enjoyed this article and want to receive more valuable industry content like this, click here to sign up for our digital newsletters!










Leave a Reply