Ransomware is evolving. New strains are popping up by the week. Phishing scams, data breaches, and new fileless ransomware are only some examples the many forms that ransomware can take.
One of the newest strains on the market, WannaCry, was released in mid-May and quickly compromised more than 200,000 computers across 150 countries. The accidental discovery of a “kill switch” in the code temporarily halted the infection, but within days new, updated strains appeared without the switch and with demands for over $200 payable by Bitcoin to have files unlocked and restored.
Even more worrisome is the fact that ransomware appears indiscriminate, targeting large and small businesses, corporate staff and consumers alike. Simply put, there’s nowhere to hide — users need effective ways to identify new ransomware, lessen the impact and improve overall security.
Rapid Revenue
Ransomware is lucrative for hackers, and terrifying for users because it works — victims don’t want to lose important documents and files, and are often willing to pay even if the malicious code isn’t that sophisticated. It makes sense: Why risk the loss of data or negative PR if a quick payment solves the problem, right? But it rarely stops there. Once attackers know a small business or user is vulnerable, they often strike again.
Socially Suspect
Typically, hackers don’t need to leverage complex or multi-level attack vectors. Emails containing seemingly legitimate attachments or links to high-value Web content are often enough to entice users, and infect computers. New security software is adapting to these methods, however, making it harder for attackers to sneak through spam defenses or run compromised Web scripts.
Cybercriminals aren’t giving up, however. Ransomware is lucrative enough that they’ve simply changed tactics to avoid emerging security solutions, and infect devices without detection.
Fileless Frustration
Consider the rise of “fileless” malware. Instead of downloading malware droppers — which may be detected by antivirus programs — fileless variants instead leverage macros in Word documents or compromised links to run PowerShell commands and execute scripts (see infographic below), which in turn contact Web servers and grab the ransomware payload. Since PowerShell is typically given unfettered system access, both users and AV programs are left in the dark.
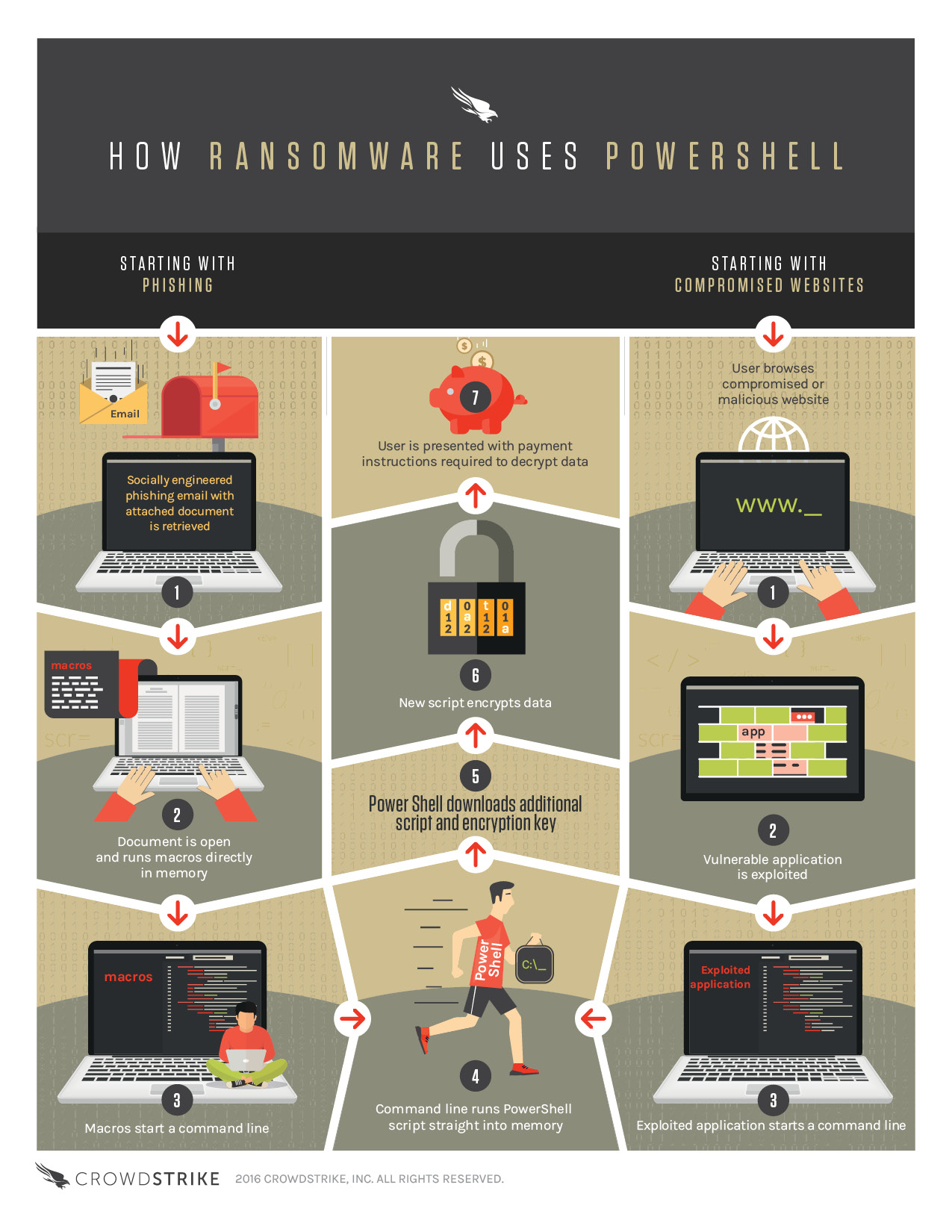 So what’s the solution to both existing and emergent ransomware threats? It starts with effective action: Disable macros by default and monitor Web traffic from all apps, not just third-party downloads. Individuals and small businesses also need detection methods that dig deeper than whitelists to identify indicators of attack (IoAs) and recommend remediation rather than waiting until data is locked and ransom demands have arrived.
So what’s the solution to both existing and emergent ransomware threats? It starts with effective action: Disable macros by default and monitor Web traffic from all apps, not just third-party downloads. Individuals and small businesses also need detection methods that dig deeper than whitelists to identify indicators of attack (IoAs) and recommend remediation rather than waiting until data is locked and ransom demands have arrived.
Ransomware is everywhere. Stay safe; learn more about emerging attack vectors and the value of emergent defense.
Author bio: Con Mallon is Senior Director of Product Marketing at CrowdStrike, where he oversees positioning of products and communication, go-to-market programs, competitive differentiation, and sales assets and tools. Con started his career in the United Kingdom, and has more than 20 years of marketing and product management experience within the technology sector.
If you enjoyed this article and want to receive more valuable industry content like this, click here to sign up for our digital newsletters!










Leave a Reply