WASHINGTON–(BUSINESS WIRE)–Here are key takeaways from BakerHostetler’s 2022 Data Security Incident Response Report issued April 7th:
- Ransomware remained the most prevalent and impactful type of data security incident. Investments in security enhancements and business continuity practices are making companies more resilient and less likely to choose to pay, driving down the average ransom payment amount. Threat actors continue to evolve tactics to increase extortion leverage, such as using publication countdown timers and contacting employees and customers directly to pressure the company to pay.
- The pandemic, technology strategy and business continuity advantages are driving increased use of cloud assets, which also changes the risk landscape and makes additional security measures, like asset management and access controls, increasingly important.
- E-crime continued, including a surge of wire fraud precipitated by gaining access to email accounts. There are concerns about e-crime actors supporting state entities as a result of the Russia/Ukraine war.
Why this matters
The 2022 Data Security Incident Response Report marks the eighth year that BakerHostetler has analyzed the data from incidents it managed in the prior year. The 2022 DSIR features insights and metrics from more than 1,270 incidents that members of the firm’s Digital Assets and Data Management Practice Group helped clients manage in 2021. This one-of-a-kind report is a mix of aggregated data from security incidents and insights from its full suite of advisory services to clients across the entire data and technology life cycle.
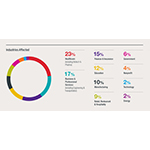
The inside cover features 19 key findings covered more in depth throughout the report, and then it is followed by a dashboard style “At a Glance” section, with 39 key incident response data points. Recurring sections from past years — on industries affected, incident response life cycle timeline, forensics, the number of incidents that resulted in regulatory investigations and litigation, ransomware, and health care deep dives — include a trove of data and analysis to help readers track substantial changes and enhance their cybersecurity posture. The DSIR also includes checklists and industry updates to help companies improve their security measures and operational resilience.
Key quote
“Implementing effective security measures is a challenge because the risk landscape is dynamic. Companies need to have one eye trained on threat intelligence while having another eye on execution and implementation. The data we collect from the thousands of incidents we have helped manage over the years enables clients to prioritize limited time, money and resources. A company that is nimble in its security strategy is likely more resilient and better positioned to leverage the value of technology to support organizational goals and missions,” said Theodore J. Kobus III, chair of BakerHostetler’s DADM Practice Group.
Ransomware is front and center — for criminals and victims
Continued ransomware attacks and several high-profile incidents have drawn increased attention to the issue from government entities and regulators, as well as the victims.
- Ransomware accounted for 37% of 2021 matters, compared to 27% in 2020.
- Attackers are resorting to double or triple extortion tactics. In an effort to increase pressure on organizations to pay a ransom, ransomware groups — in addition to encrypting files to cause an outage — threaten to publish stolen data and add other tactics such as distributed denial of service attacks to further disrupt operations.
- In 2021 ransomware matters, threat actors claimed to have stolen data 82% of the time. This is compared to 70% of the time in 2020, a continuation of a trend that first emerged late that year.
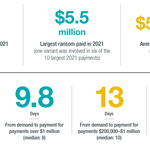
- The average ransom paid decreased to $511,957, roughly a 30% reduction from the average amount paid in 2020; this was the first drop after years of increases. Organizations took longer to pay, paying after eight days (median) compared with five days in 2020. This mostly reflects better business continuity practices; organizations were more often able to restore from backups and were paying to prevent publication so negotiations can be stretched out.
Key quote
“A key difference between organizations that had meaningful ransomware events and those that did not was the use of a fully deployed endpoint detection and response tool that was set in enforcement mode with the anti-uninstall feature enabled. Organizations that were affected by a ransomware attack in 2021 were more likely to have effective backups to restore from. Ransomware attacks are not going away. In addition to an EDR tool and a robust business continuity plan, effective measures to combat this risk include multi-factor authentication, effective patch management and addressing remote desktop protocol,” said Craig Hoffman, co-leader of BakerHostetler’s national Digital Risk Advisory and Cybersecurity team. “These measures apply to both the organization and its vendors.”
Litigation on the rise, particularly for smaller incidents
In 2021, multiple lawsuits were filed in the same venue within weeks following incident notification, even for smaller events. There have also been handfuls of related cases filed in one federal forum and another handful of related cases filed in state venues. This duplicative litigation trend is increasing the initial defense costs and the ultimate cost of settlement because of the number of plaintiffs’ attorneys involved.
- Of the incidents included in the 2022 report, 23 resulted in one or more lawsuits.
- Nineteen incidents involved Social Security numbers, five involved payment card data, three started with system misconfiguration, 16 involved medical/health information, 15 involved ransomware and four were vendor related.
- Number of lawsuits filed by individuals notified: More than 1.2 million individuals — eight lawsuits; fewer than 700,000 individuals — eleven lawsuits; fewer than 8,000 individuals — three lawsuits.
- 58+ lawsuits were filed related to the 23 incidents. Eight incidents had more than one (but less than five) lawsuits filed—four incidents had five or more lawsuits filed—and 43 of the 58+ lawsuits were against a healthcare organization.
Fraudulent fund transfer incidents persist
Business email compromises, or BECs — phishing and social engineering attacks leading to unauthorized access to email accounts that are then used to trick organizations into wiring money to a threat actor-controlled bank account because they believe they are sending the money to the correct account — have been around for years. The prevalence slowed at the start of the pandemic and then surged in 2021.
- We saw an increase in the number of BECs that resulted in the organization having to provide notification of the incident to individuals/regulatory agencies — 60% of the time, up from 43% in 2020.
- The recovery rate increased in 2021. Funds involved in fraudulent fund transfer schemes last year were recovered 43% of the time, up from the 38% recovery rate BakerHostetler saw in 2020. There is a very effective unit of the Secret Service that works on recovery of funds.
BakerHostetler’s DADM Practice Group is a convergence practice addressing enterprise risks, disputes, compliance and opportunities throughout the life cycle of data, technology, advertising and innovation, including brand strategies and monetization. The practice group integrates seven service teams — digital risk advisory and cybersecurity; advertising, marketing and digital media; privacy governance and technology transactions; health care privacy and compliance; privacy and digital risk class action and litigation; digital transformation and data economy; and emerging technology.
For more information on BakerHostetler’s DADM Practice Group, visit https://www.bakerlaw.com/DigitalAssetsDataManagement. Connect with us on Twitter at @BakerHostetler or on LinkedIn at @BakerHostetler, @TedKobus and @CraigHoffman.
About BakerHostetler
With scores of highly ranked attorneys across multiple practice areas, BakerHostetler helps clients around the world address their most complex and critical business and regulatory issues, delivering sophisticated counsel and outstanding client service. The firm has six core practice groups — Business, Digital Assets and Data Management, Intellectual Property, Labor and Employment, Litigation, and Tax — composed of more than 1,000 lawyers located coast to coast. For more information, visit bakerlaw.com.
Contacts
Courtney B. Smith
202-861-1514
[email protected]
Diego Catala
202-861-1515
[email protected]
If you enjoyed this article and want to receive more valuable industry content like this, click here to sign up for our digital newsletters!