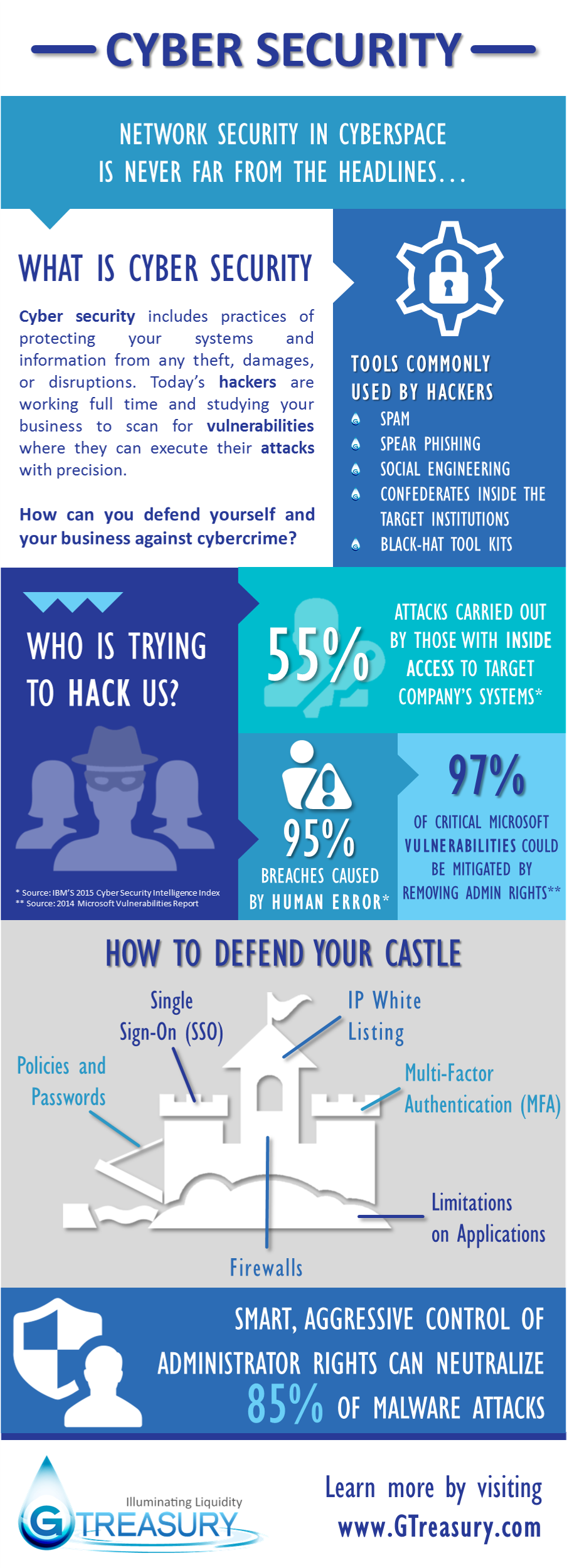
What is cyber security?
That’s the question that GTreasury, a company that offers a Treasury Management System (TMS), attempts to answer in a recent infographic.
First, a primer on what some of the terms surrounding cyber security mean:
- Spam is electronic junk mail. The term refers to unsolicited, and often times unwanted, email.
- Spear Phishing is a type of highly specialized attacks against specific targets to collect information and or gain access to systems. A common example of spear phishing is when a cybercriminal initiates an attack on a business to gain access to the network. From there, the criminal is able to send emails that look authentic and can easily make it through spam filters.
- Social Engineering attacks involve manipulation of users and employees to offer confidential and sensitive data. These types of attacks usually involve email to invoke fear and urgency, forcing the unsuspecting victim to share information by opening a malicious file or click a harmful link. It is a type of confidence trick for the purpose of information gathering, fraud, or system access. It differs from a traditional “con” in that it is often one of many steps in a more complex fraud scheme.
- Confederates Inside the Target Institutions refers to a group of cybercriminals of which one or more are secretly working from within the targeted institution. These ‘inside men’ can use social engineering, theft, or other nefarious means to aid their colleagues outside the institution.
- Black-Hat Tool Kits are a set of tools whose initial purpose was to provide researchers with the means to test the security of networks and devices. However, they are often used by hackers, “black hats”, to break into networks.
- Single sign-on (SSO) is a method of access control for multiple related, but independent software systems. With SSO a user logs in with a single ID and password to gain access to a connected system or systems without using different usernames or passwords, or in some configurations seamlessly sign on at each system. Conversely, single sign-off is the property whereby a single action of signing out terminates access to multiple software systems.
- IP White Listing is a term for a list of email addresses or IP addresses that are deemed spam free. The list overrides blacklists and spam filters, allowing emails to be delivered to a users inbox rather than filtered out as spam.
- Multi-Factor Authentication is a type of access control where a user is only granted access after providing several separate pieces of information for authentication. Typically at least two of the following categories: knowledge (something they know), possession (something they have), and inherence (something they are).
- A firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed not to be secure or trusted.
Cyber Security was created by GTreasury, a leading provider of treasury management systems.
If you enjoyed this article and want to receive more valuable industry content like this, click here to sign up for our digital newsletters!










Leave a Reply